




Enterprise Risk and Process Management helps on Inconsistency Processes
A security process risk management platform streamlines critical security tasks and processes across an organization. It offers a unified solution that enables security teams to efficiently manage, monitor, and execute security workflows. By managing repetitive tasks, this platform enhances response times, reduces manual errors, and ensures consistent compliance with security protocols, allowing teams to focus on higher-priority threats and strategies.
Enterprise Risk and Process Management helps on Inconsistency Processes
A security process risk management platform streamlines critical security tasks and processes across an organization. It offers a unified solution that enables security teams to efficiently manage, monitor, and execute security workflows. By managing repetitive tasks, this platform enhances response times, reduces manual errors, and ensures consistent compliance with security protocols, allowing teams to focus on higher-priority threats and strategies.
Security Risk and Process Management Platform
- Risk Management
- Software Security
- Standards & Compliance
- Incident Response
- Third Party Risk
The Organization Security Posture and Asset Risk Monitoring modules deliver comprehensive visibility into a client’s security posture, helping identify vulnerabilities and areas for improvement. These modules foster collaboration across security, IT, and compliance teams by offering a centralized platform to manage and monitor security processes. With real-time insights and actionable data, organizations can enhance risk management, streamline communication, and proactively address potential security gaps, ensuring a stronger and more resilient security infrastructure.
These solutions empower clients to manage software security and enforce secure development practices, minimizing the organization’s exposure to security breaches and vulnerabilities. The User Management, Change Request Process Automation, PDINPE Request Automation, DPIA Process Automation, and DSR Response Automation modules are designed to automate and optimize manual workflows. By streamlining these processes, organizations can save time, reduce operational risks, and enhance accuracy, all while ensuring compliance with regulatory requirements and industry best practices.
This automation strategy, aligned with international cybersecurity standards and compliance requirements, enables organizations to achieve greater efficiency, consistency, and security in their compliance efforts. A centralized dashboard offers real-time visibility into the organization’s compliance posture, allowing for proactive identification of potential issues. By detecting compliance gaps early, organizations can take timely corrective actions, reducing the risk of non-compliance and ensuring continuous adherence to regulatory standards.
The Incident Response Management module enables clients to efficiently manage and respond to security incidents, minimizing downtime and mitigating the risk of costly consequences. By leveraging Incident Response Process Automation, an Incident Response Plan, and IR Playbooks, organizations can ensure a standardized and effective approach to incident handling. This not only streamlines response efforts but also strengthens the organization’s overall security posture, enhancing resilience against potential threats and vulnerabilities.
This module can help clients to effectively manage third-party risks, including vendor security review assessments and vendor management, reducing the organization’s exposure to security breaches.
Security Risk and Process Management Platform
- Risk Management
- Software Security
- Standards & Compliance
- Incident Response
- Third Party Risk
The Organization Security Posture and Asset Risk Monitoring modules deliver comprehensive visibility into a client’s security posture, helping identify vulnerabilities and areas for improvement. These modules foster collaboration across security, IT, and compliance teams by offering a centralized platform to manage and monitor security processes. With real-time insights and actionable data, organizations can enhance risk management, streamline communication, and proactively address potential security gaps, ensuring a stronger and more resilient security infrastructure.
These solutions empower clients to manage software security and enforce secure development practices, minimizing the organization’s exposure to security breaches and vulnerabilities. The User Management, Change Request Process Automation, PDINPE Request Automation, DPIA Process Automation, and DSR Response Automation modules are designed to automate and optimize manual workflows. By streamlining these processes, organizations can save time, reduce operational risks, and enhance accuracy, all while ensuring compliance with regulatory requirements and industry best practices.
This automation strategy, aligned with international cybersecurity standards and compliance requirements, enables organizations to achieve greater efficiency, consistency, and security in their compliance efforts. A centralized dashboard offers real-time visibility into the organization’s compliance posture, allowing for proactive identification of potential issues. By detecting compliance gaps early, organizations can take timely corrective actions, reducing the risk of non-compliance and ensuring continuous adherence to regulatory standards.
The Incident Response Management module enables clients to efficiently manage and respond to security incidents, minimizing downtime and mitigating the risk of costly consequences. By leveraging Incident Response Process Automation, an Incident Response Plan, and IR Playbooks, organizations can ensure a standardized and effective approach to incident handling. This not only streamlines response efforts but also strengthens the organization’s overall security posture, enhancing resilience against potential threats and vulnerabilities.
This module can help clients to effectively manage third-party risks, including vendor security review assessments and vendor management, reducing the organization’s exposure to security breaches.
When Everything can be Smart, why not our Approach to Security?
Empower your Decision-Making skills with a hassle-free Cyber Security Management.
It's time to translate your cyber security strategy and vision into actions
Empower your Decision-Making skills with a hassle-free Cyber Security Management.
Security is the present Digital era's on demand necessity...
Empower your Decision-Making skills with a hassle-free Cyber Security Management.
Cybersecurity is not only an IT problem, it is an enterprise wide challenge
Empower your Decision-Making skills with a hassle-free Cyber Security Management.
Communicating Cyber security to the leadership is now made easy
Empower your Decision-Making skills with a hassle-free Cyber Security Management.

Beyond Securing and Safeguarding
When Everything can be Smart, why not our Approach to Security??
Beyond Securing and Safeguarding
It's time to translate your cyber security strategy and vision into actions
Beyond Securing and Safeguarding
Security is the present Digital era's on demand necessity...
Beyond Securing and Safeguarding
Cybersecurity is not only an IT problem, it is an enterprise wide challenge
Beyond Securing and Safeguarding
Communicating Cyber security to the leadership is now made easy
Your Complete Cyber Security Package
Cyber Unified redefines the security strategies around People-Process-Technology, the three robust pillars for any organization which impacts the cyber security approach and governance policies.
Customization On Finger Tips
How about having your own process flows for security assessment, vulnerability management and risk analysis?
Independent Like Never Before
Be your own boss in managing Audits, Certificates, Dashboards and Cyber Security Governance.
Securely Secured
Experience how our technical expertise can armor your security with enhanced innovation and intelligence.
Customization On Finger Tips
How about having your own process flows for security assessment, vulnerability management and risk analysis?
Independent Like Never Before
Be your own boss in managing Audits, Certificates, Dashboards and Cyber Security Governance.
Securely Secured
Experience how our technical expertise can armor your security with enhanced innovation and intelligence.
Data Privacy and Protection
The Digital world today cannot survive without the two most important promises - Privacy and Data Protection. Amidst of the plenty of available options, what if you have a solution which speaks your mind and adjusts to your environment? Cyber unified is one such platform where our customers can design their own Privacy and Data protection policies and processes.
24/7/365 Support
A product or any service kicks off only when the support services reach the user expectations with more transparency. Cyber Unified promises to guide our customers hand -in-hand while using our product/ services when and wherever they require. We ensure that our customers are highly satisfied with the product results by guiding them through the right innovation lanes.
Integrated Risk Management
Effective risk management will be always a core aspect of governance and must be embedded within the organization. It is considered as one of the key factors which impacts Decision Making. Cyber Unified streamlines your approach to manage and prioritize set of risks through an intelligently embedded and integrated risk management system. So, confidently take the next right step.
Secure SDLC
Software is a hacker’s primary target. If they can access it through web applications, your defense mechanism should focus on securing the application. The best opportunity to reduce the business impact of any incident is only through forecasting. Cyber Unified can be your best-chosen partner to encounter such unpredicted attacks while preventing the risks at the same time.
Your Complete Cyber Security Package
Cyber Unified redefines the security strategies around People-Process-Technology, the three robust pillars for any organization which impacts the cyber security approach and governance policies.
 Customization On Finger Tips
Customization On Finger Tips
How about having your own process flows for security assessment, vulnerability management and risk analysis?
 Independent Like Never Before
Independent Like Never Before
Be your own boss in managing Audits, Certificates, Dashboards and Cyber Security Governance.
 Securely Secured
Securely Secured
Experience how our technical expertise can armor your security with enhanced innovation and intelligence.
Customization On Finger Tips
How about having your own process flows for security assessment, vulnerability management and risk analysis?
Independent Like Never Before
Be your own boss in managing Audits, Certificates, Dashboards and Cyber Security Governance.
Securely Secured
Experience how our technical expertise can armor your security with enhanced innovation and intelligence.
Data Privacy and Protection
The Digital world today cannot survive without the two most important promises - Privacy and Data Protection. Amidst of the plenty of available options, what if you have a solution which speaks your mind and adjusts to your environment? Cyber unified is one such platform where our customers can design their own Privacy and Data protection policies and processes.
24/7/365 Support
A product or any service kicks off only when the support services reach the user expectations with more transparency. Cyber Unified promises to guide our customers hand -in-hand while using our product/ services when and wherever they require. We ensure that our customers are highly satisfied with the product results by guiding them through the right innovation lanes.
Integrated Risk Management
Effective risk management will be always a core aspect of governance and must be embedded within the organization. It is considered as one of the key factors which impacts Decision Making. Cyber Unified streamlines your approach to manage and prioritize set of risks through an intelligently embedded and integrated risk management system. So, confidently take the next right step.
Secure SDLC
Software is a hacker’s primary target. If they can access it through web applications, your defense mechanism should focus on securing the application. The best opportunity to reduce the business impact of any incident is only through forecasting. Cyber Unified can be your best-chosen partner to encounter such unpredicted attacks while preventing the risks at the same time.
AUTRIGO- Your First Step towards Smarter Security Approach
AUTRIGO delivers a comprehensive, integrated enterprise cyber risk management solution, offering a unified platform for compliance control automation and risk evaluation. This all-in-one solution addresses the full spectrum of cybersecurity processes and service requirements across the organization, enabling streamlined management and enhanced protection against evolving threats. With AUTRIGO Platform, organizations can ensure robust compliance and risk mitigation while maintaining operational efficiency.
- Digital Asset Management
- Standard Frameworks
- Data Privacy and Protection
- Vendor Security Review
- Secure SDLC
- Continues Risk Monitoring
- Security Incident Management
- Security Change Request
- Risk Acceptance
- PDINPE
Digital Asset Risk Management
Welcome to Cyber Unified’s Digital Asset Management module, engineered to help you effectively identify, protect, and monitor your organization’s digital assets. In an increasingly complex digital landscape, businesses encounter heightened risks to their valuable data. Our robust solution empowers you to proactively manage these risks, optimize asset utilization, and ensure the confidentiality, integrity, and availability of your critical digital assets, safeguarding your organization's most valuable information against evolving threats.
Know More
International Standard Frameworks
In today’s evolving threat landscape, organizations face the ongoing challenge of protecting their assets from cyber risks. Cyber Unified offers a comprehensive solution that leverages internationally recognized frameworks to help businesses not only meet compliance standards but also implement effective risk management strategies. Our International Standards and Frameworks Compliance Assessments enable organizations to adopt industry best practices, equipping security and compliance teams with the tools needed to identify, understand, and mitigate risks across the enterprise, ensuring a robust and resilient security posture.
Know More
Data Privacy and Protection Assessment
In an era where data privacy is critical, organizations must continuously evaluate and improve their practices. Cyber Unified's Data Privacy and Protection Assessment offers a comprehensive evaluation of an organization's data privacy practices, providing actionable recommendations for enhancement. This assessment ensures regulatory compliance, satisfies oversight requirements, and fosters a culture of data privacy and protection. In this content, we will explore the key benefits of Cyber Unified’s assessment and how it empowers organizations to safeguard sensitive information effectively.
Know More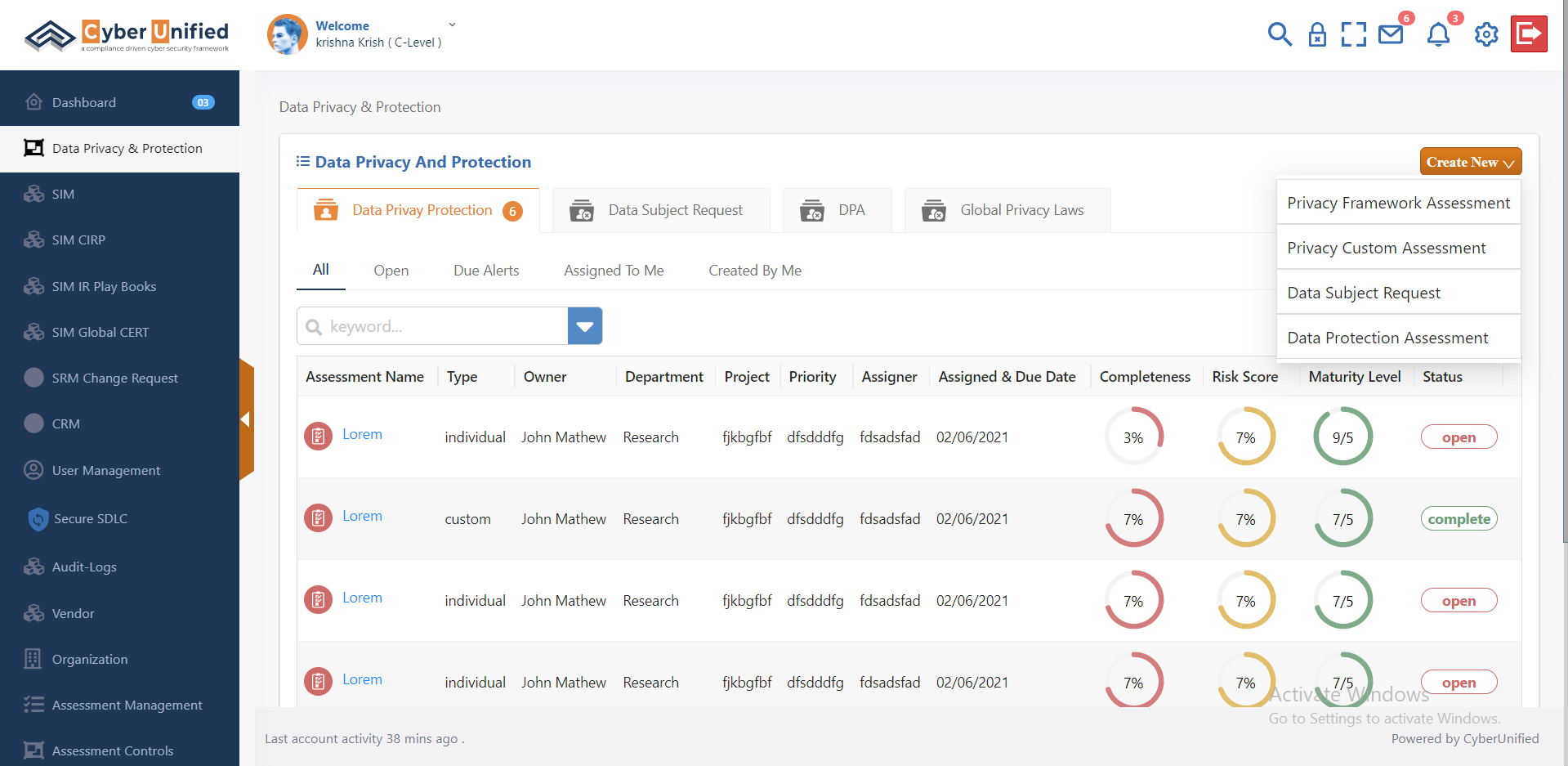
Third-Party Security Review (VRM)
In today’s interconnected business environment, organizations increasingly depend on third-party vendors to support critical operations. However, this reliance introduces the challenge of ensuring that these vendors meet cybersecurity standards and minimize risks to sensitive data and systems. Cyber Unified’s Vendor Risk Management (VRM) module provides a comprehensive solution to assess, monitor, and mitigate risks associated with third-party vendors. This content will explore the key features and benefits of Cyber Unified’s VRM module, demonstrating how it helps organizations streamline their vendor risk management processes effectively.
Learn More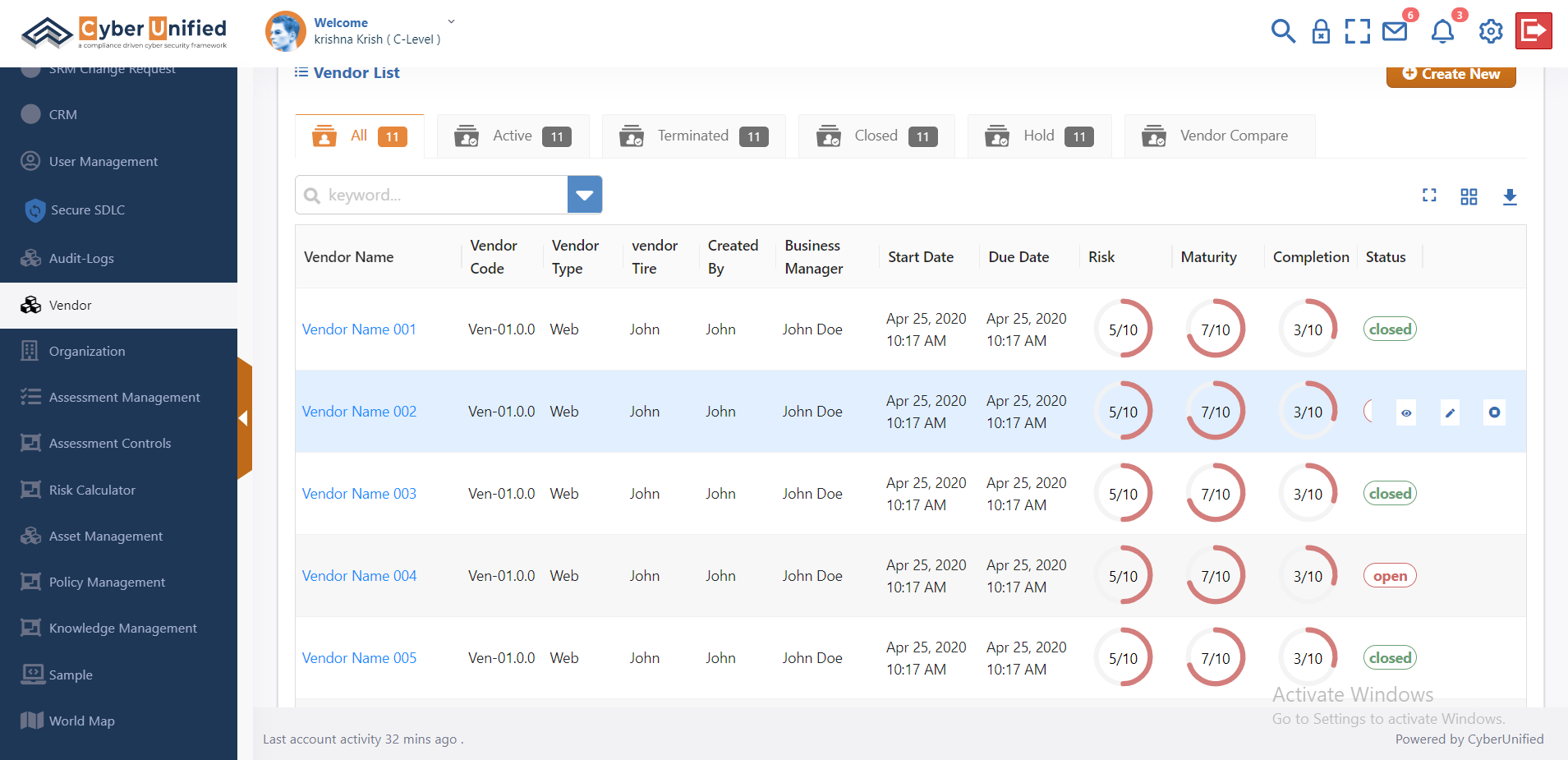
Secure SDLC
In today’s digital environment, securing software applications throughout their development lifecycle is crucial. Secure Software Development Life Cycle (SDLC) assessments are essential for identifying and mitigating potential security risks. However, traditional manual assessment processes can be time-consuming and prone to errors. Cyber Unified’s Secure SDLC Assessment Automation provides a robust solution to streamline and automate secure SDLC assessments. This module enhances application security and minimizes vulnerabilities by optimizing the assessment process. Explore the key features and benefits of Cyber Unified’s Secure SDLC Assessment Automation module to elevate your application security and efficiency.
Know More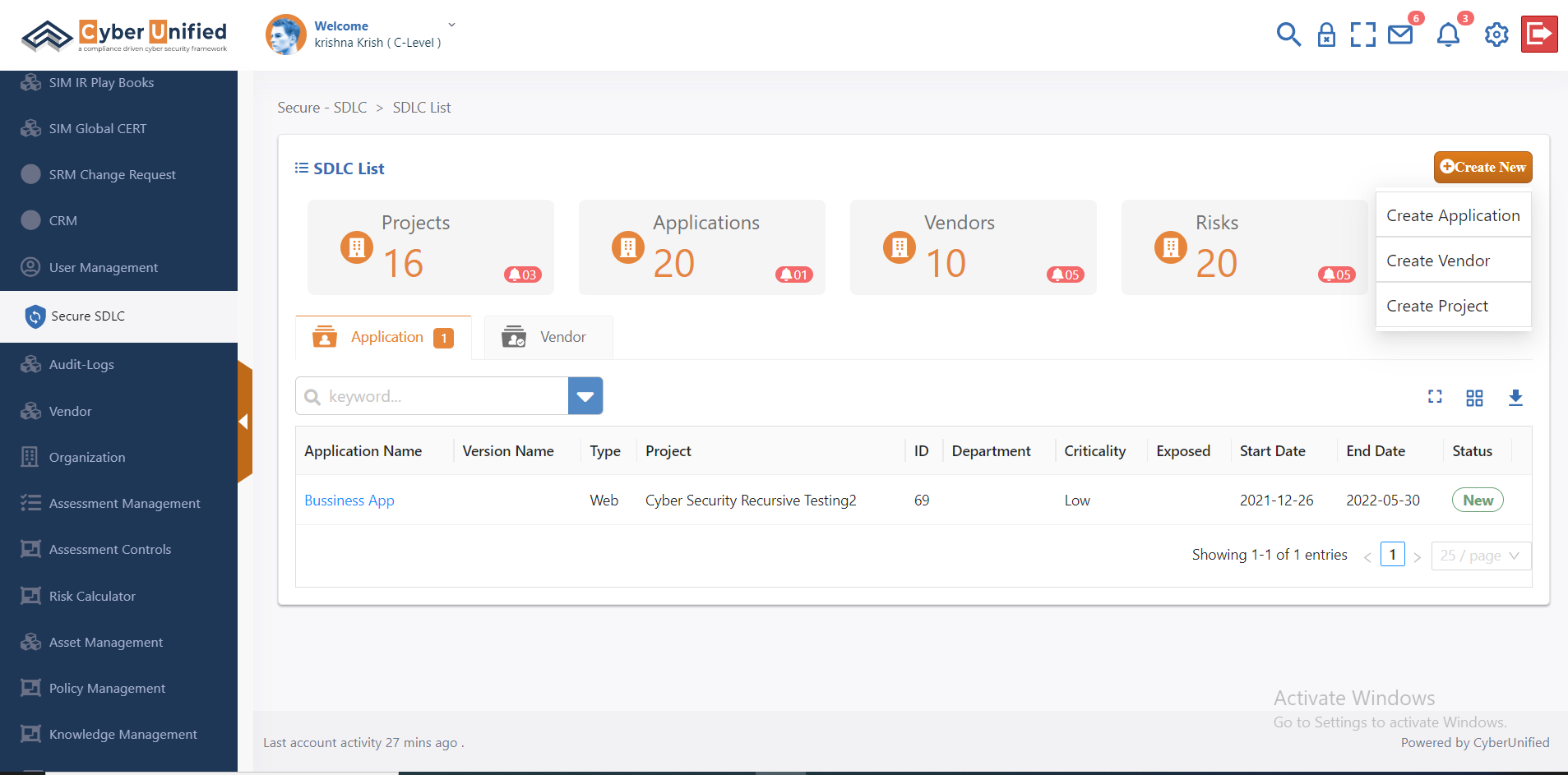
Continues Risk Monitoring / Vulnerability Management
In today’s dynamic digital environment, organizations encounter a wide array of cybersecurity threats that can impact their operations and reputation. Proactively managing and mitigating these risks is essential for sustaining a robust security posture and ensuring business continuity. Cyber Unified’s Risk Response Management Automation offers a comprehensive solution to streamline risk management processes. Our automation module enables organizations to efficiently monitor, assess, and address cyber risks, empowering you to navigate the complex risk landscape with confidence and safeguard your critical assets.
Know More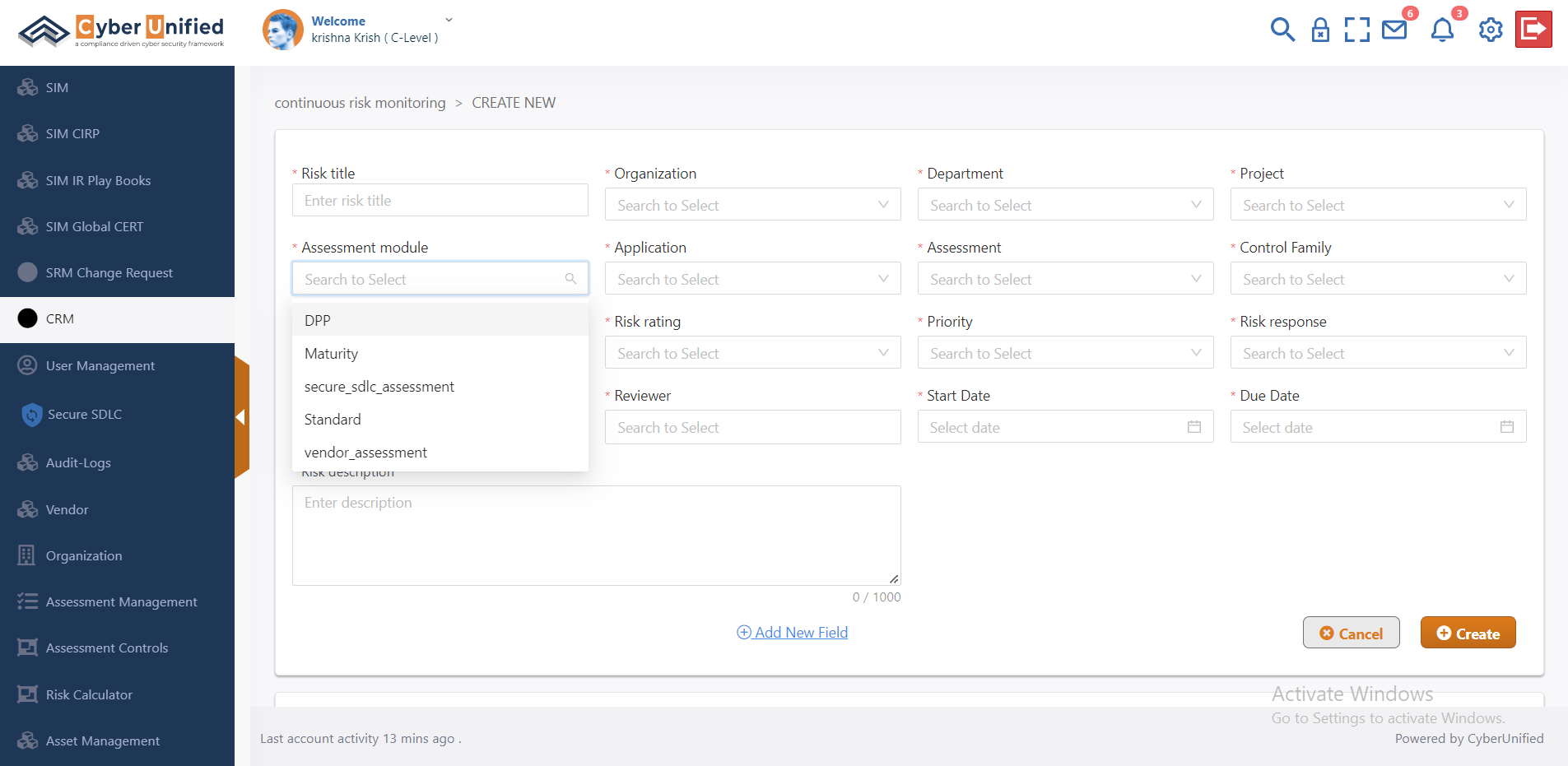
Security Incident Management
Effectively managing and responding to cybersecurity incidents is crucial for minimizing impact and avoiding significant repercussions. Cyber Unified’s Incident Response Process Automation module elevates your incident response capabilities by providing a comprehensive solution for managing and monitoring all cybersecurity incidents. Our module ensures a swift, standardized response, enabling you to handle incidents efficiently and maintain a robust security posture. Discover how our automation module can transform your incident response process.
Know More
Security Change Request
Welcome to our Security Change Request Process Automation module. In today’s fast-paced cybersecurity environment, effectively managing and implementing security changes is essential. Our solution provides robust automation capabilities designed to streamline the change request process, enhance visibility, and uphold stringent security controls. Explore the key benefits and features of our Security Change Request Automation module and discover how it can optimize your security management practices.
Know More
Risk Acceptance
Cyber Unified’s Risk Acceptance Automation—a state-of-the-art solution transforming how organizations handle and oversee security risk acceptance. Our advanced platform delivers enhanced risk visibility, optimized workflows, and actionable insights, empowering organizations to make informed decisions and effectively assess risks. Discover the key benefits of our solution and how it can elevate your risk management strategy.
Know More
PDINPE (Production Data In Non-Production Environment)
Effectively managing production data in non-production environments is essential for organizations to support testing, development, and training activities while safeguarding the security and integrity of sensitive data. Cyber Unified offers an advanced solution to automate the Production Data in Non-Production Environment (PDINPE) process, delivering significant benefits to organizations. In this website content, we will highlight the advantages of Cyber Unified’s PDINPE module and how it streamlines the secure management of production data across non-production environments.
Know More

Your Complete Cyber Security Package
Empower your decision-making skills with automated cyber security process management.
-
Securely Secured
Experience how our technical expertise can armor your security with enhanced innovation and intelligence.
-
Independent Like Never Before
Be your own boss in managing Audits, Certificates, Dashboards and Cyber Security Governance.
-
Customization On Finger Tips
How about having your own process flows for security assessment, vulnerability management and risk analysis?

Our Services- Your Success Stories
Our extensive capabilities cover the full spectrum of information security. We provide a comprehensive suite of services designed to help you craft a robust strategy, identify threats and risks, implement the right technologies, and ensure operational preparedness, empowering your business with enhanced security.
Governance and Compliance Assessments
Smart evaluation is now on your finger tips. Maintaining compliance with regulations not only requires significant knowledge and understanding, but can also be expensive and resource intensive




Risk Assessment
A timely and smart risk assessment is what we offer to our clients. The purpose of Risk Management is to identify, analyze, and mitigate risks to critical service assets that could adversely affect the operation and delivery of services.




Application Security in SDLC
Secure your application’s market value with trusted services. Every application holds a market value and security threat throughout its development lifecycle.




Third Party (Vendor) Security Review
It’s time to think beyond the regular security protection. It is very important to review the security of your vendors before you engage them, to make sure they are capable of meeting your needs




Network Vulnerability Assessment
It’s time to challenger the vulnerabilities now. Network devices are commonly targeted by hackers in order to threaten the entire network or to steal information.




Cyber Security Maturity Review
Your future decisions are securely reviewed from now on. Cyber Security Maturity Review will help the organization address their security gaps, plan a security roadmap through clear guidance, assessment and best practices,




Cyber Resilience Review
A smart and well-practiced security approach like never before. The Review is designed to measure existing organizational resilience as well as provide a gap analysis for improvement based on recognized best practices.




- Governance & Compliance
- Risk Assessment
- Application Security in SDLC
- Third Party Security Review
- Network Vulnerability Audit
- Cyber Security Maturity
- Cyber Resilience Review
Governance and Compliance Assessments
At CuberUnified, we offer a cutting-edge solution for governance and compliance assessments that simplifies the process. Our streamlined approach ensures a smart evaluation tailored to your specific needs, saving you time, money, and valuable resources.
👉 Know More




Risk Assessment
At CyberUnified, we offer comprehensive risk assessment services designed to empower our clients with strategic insights and proactive risk management solutions. Our expert team is dedicated to understanding your unique business landscape, enabling us to identify and assess risks that may impact your operations.




Application Security in SDLC
At CyberUnified, we offer comprehensive application security services designed to safeguard your application at every stage of the software development lifecycle (SDLC). Our expert team is dedicated to ensuring that your application is fortified against potential security breaches and vulnerabilities, allowing you to deliver a secure and reliable product to your users.




Third Party (Vendor) Security Review
At CyberUnified, we offer comprehensive third-party security review services designed to assess the security posture of your vendors. Our expert team specializes in evaluating the security practices and controls of potential vendors, providing you with valuable insights to make informed decisions and mitigate risks associated with vendor engagements.




Network Vulnerability Assessment
At CyberUnified, we provide comprehensive network vulnerability assessment services designed to proactively identify and address vulnerabilities within your network infrastructure. Our expert team specializes in evaluating your network devices, ensuring they are fortified against potential threats and providing you with actionable insights to enhance your network security.




Cyber Security Maturity Review
At CyberUnified, we offer a comprehensive Cyber Security Maturity Review service designed to evaluate the effectiveness and maturity of your organization's security measures. Our expert team conducts a thorough assessment, providing you with clear guidance, actionable recommendations, and a roadmap to enhance your cyber security posture.




Cyber Resilience Review
At CyberUnified, we offer a comprehensive Cyber Resilience Review service that evaluates your organization's ability to withstand and recover from cyber threats. Our expert team conducts a thorough assessment, enabling you to measure your resilience and receive actionable recommendations for improvement.




- Governance & Compliance
- Risk Assessment
- Application Security in SDLC
- Third Party Security Review
- Network Vulnerability Audit
- Cyber Security Maturity Review
- Cyber Resilience Review
Industry Expertise
Cybersecurity compliance spans multiple sectors, each with distinct regulations governing data security, integrity, and accessibility. Cyber Unified recognizes and respects the unique cybersecurity goals of each industry, ensuring alignment with their specific compliance requirements and safeguarding their data in accordance with industry standards.
Financial Services
Security is paramount in the financial sector, which faces significant challenges, particularly in protecting online payments and sensitive credit card information. A robust security posture, such as that offered by Cyber Unified, is essential to safeguard financial transactions. Compliance requirements in the financial industry vary by region and are inherently complex, demanding tailored and comprehensive security solutions.
Manufacturing
Although the manufacturing sector employs various security algorithms, it is essential to adopt a tailored safety approach for each specific category. Cyber Unified delves deeply into the unique needs of the manufacturing industry, ensuring strict adherence to its security policies, standards, and compliance regulations, providing a comprehensive and industry-specific security solution.
Healthcare
The healthcare industry manages vast amounts of sensitive data, including patient information, transaction details, pharmaceutical data, and equipment records. Protecting this data-rich environment is crucial and requires a sophisticated security approach like Cyber Unified’s comprehensive security mechanism. Our solution safeguards both Critical Infrastructure Operations (CIO) and Protected Health Information (PHI), ensuring the integrity and security of healthcare systems.
Retail
The retail industry is frequently a prime target for data theft and cyber-attacks. As a key player in handling sensitive transactions, it adheres to critical security regulations such as PCI-DSS, which governs transaction security. However, to fully safeguard Point-of-Sale (POS) systems and Personally Identifiable Information (PII), a comprehensive cybersecurity solution like Cyber Unified is essential for robust protection against evolving threats.
Government
Government bodies worldwide manage vast, complex datasets that present significant challenges in terms of safeguarding and security. These large-scale data repositories require continuous, robust cybersecurity protection. A sophisticated solution like Cyber Unified is well-equipped to handle these demands, providing comprehensive and ongoing protection for sensitive government data.
IT Sector
The IT sector remains one of the most frequently targeted industries for cyber-attacks, with threats often originating from omnichannel attacks and vulnerabilities within supply chain networks. Cyber Unified offers a cutting-edge solution to proactively detect and defend against these sophisticated attacks, providing robust protection for your IT infrastructure.
Our Blogs
Cyber Unified delivers an all-in-one enterprise cyber risk management solution, integrating compliance control automation and risk evolution. This comprehensive platform addresses all cybersecurity processes and service requirements across the organization, ensuring streamlined, end-to-end protection and compliance.

- Uncategorized
- 2023-09-09
India’s Digital Personal Data Protection Bill 2023: A Comprehensive Overview

- Uncategorized
- 2023-07-23
Strengthening Vendor Security with Cyber Unified’s Third-Party Security Assessment (VRM)

- Uncategorized
- 2023-07-23
Enhancing Cyber Security with Cyber Unified’s International Standard Frameworks

- Uncategorized
- 2023-07-23
Enhancing Incident Response Efficiency with Automation: Cyber Unified’s Incident Response Process
What Client’s Say About Us
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Quis ipsum suspendisse ultrices gravida. Risus commodo viverramaecenas accumsan lacus vel facilisis.

Kilva Dew
DeveloperLorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Quis ipsum suspendisse ultrices gravida. Risus commodo viverramaecenas accumsan lacus vel facilisis.

Axon Detos
CEOLorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Quis ipsum suspendisse ultrices gravida. Risus commodo viverramaecenas accumsan lacus vel facilisis.

John Dona
DesignerLorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Quis ipsum suspendisse ultrices gravida. Risus commodo viverramaecenas accumsan lacus vel facilisis.

Jon Smith
DeveloperLorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Quis ipsum suspendisse ultrices gravida. Risus commodo viverramaecenas accumsan lacus vel facilisis.

Alien Dew
ManagerLorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Quis ipsum suspendisse ultrices gravida. Risus commodo viverramaecenas accumsan lacus vel facilisis.















